Prepping for OSCP
Goodbye QA tester career, Hello Pen tester career!
I was software QA tester for 4 years, I enjoyed working with my co workers and my team. They are great people however the work itself can be monotonous. Find myself often gazing out the window, pondering what I could have been. Eventually I got laid off with everybody else due to contract expiration and another company won the bid. Now here I contemplate on what career I should venture into.
Penetration tester
A guy who is currently my mentor encouraged to try pen testing and I like it so far! Learning to do some “black hat” hacking on HackTheBox and using brute-forcing was exciting, but mentor said to hold the horse!
you can’t do brute force anywhere in the world professionally so don’t spend too much time on it. Criminal hackers can brute force, but for work or bug bounties, brute force is not allowed.
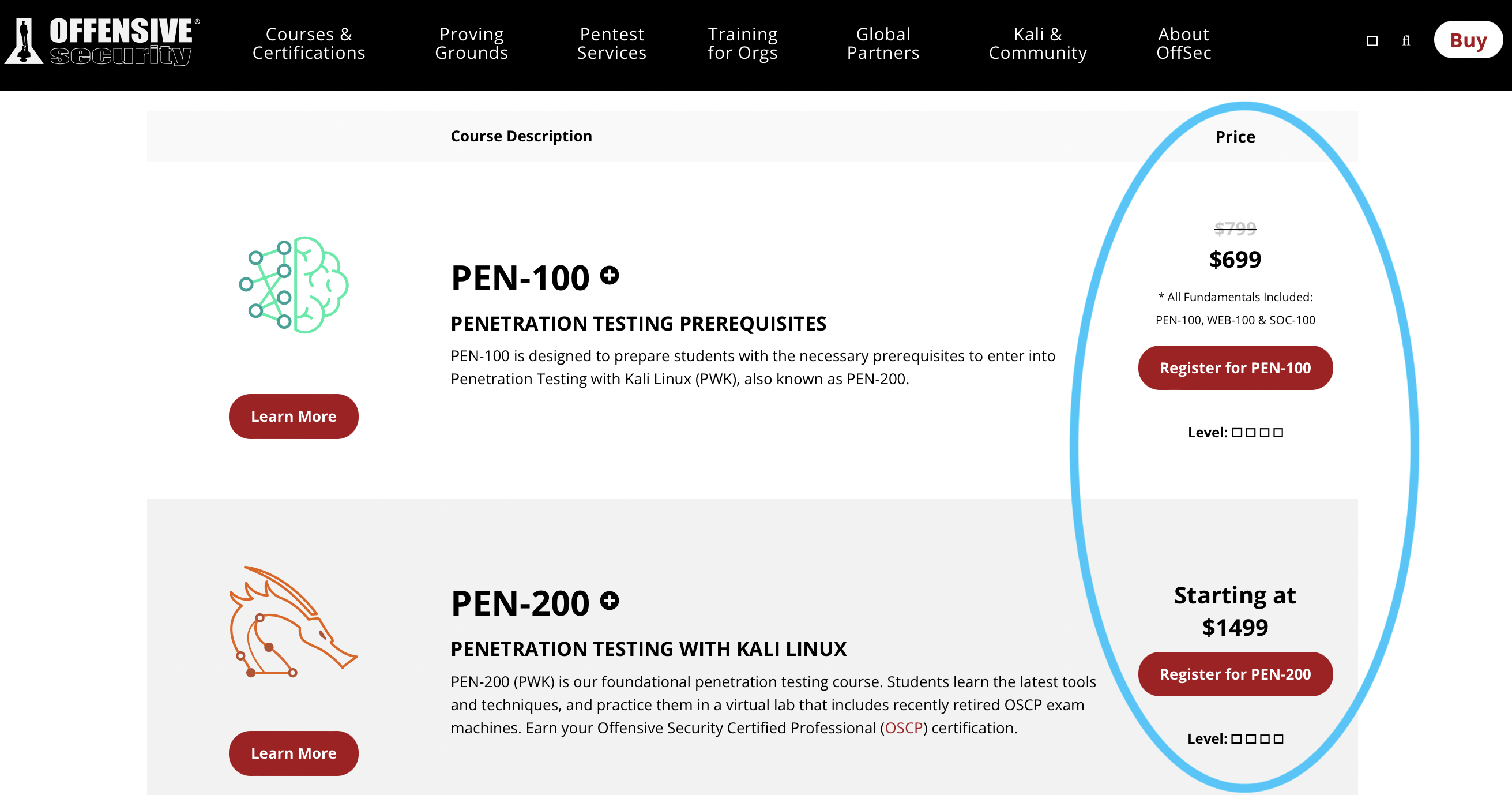
Quote unquote, he then said “OSCP is the gold standard”. Also that I’ll have to take PEN 200 course to pass the exam. He suggested on taking PEN 100 course first. Well grab popcorns on and take a look below.
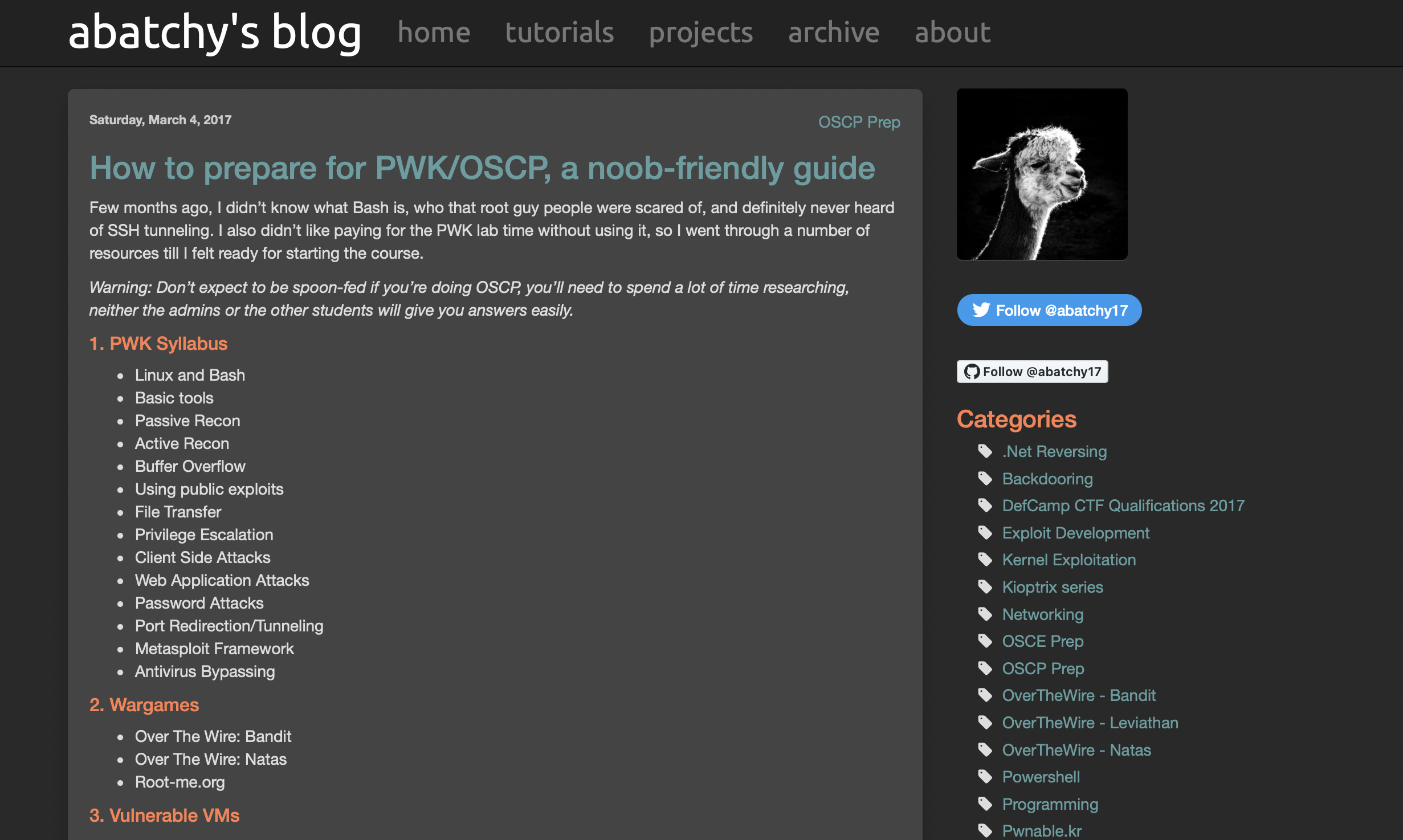
Did you see that?! 699 + 1499 = $2,198 I am pretty sure I could do without PEN 100 and found this gem abatchy.com. It got a cute avatar showing llamma or alpaca, probably the latter. Meanwhile following abatchy’s guide, I have been researching on successful pen testers/hackers in the world. Most of them are proficient in Python. I programmed in python 10 years ago and it was for a year long before dived into JavaScript and Java. I need to pick up and restore my old forgotten skills. Automate The Boring Stuff seems like a great free way to relearn Python.
Now what?
This is embarrassing as you can see I posted once every two year since 2019. This ends now. I am going to be dedicated in blogging on my learning progress. OSCP exam is the ultimate boss to face. I will be dabbling HTB while learning from abatchy’s guide, until I am ready to upgrade to Offensive Security’s Proving Grounds. Cheers!

Comments powered by Disqus.